Category: Articles
-
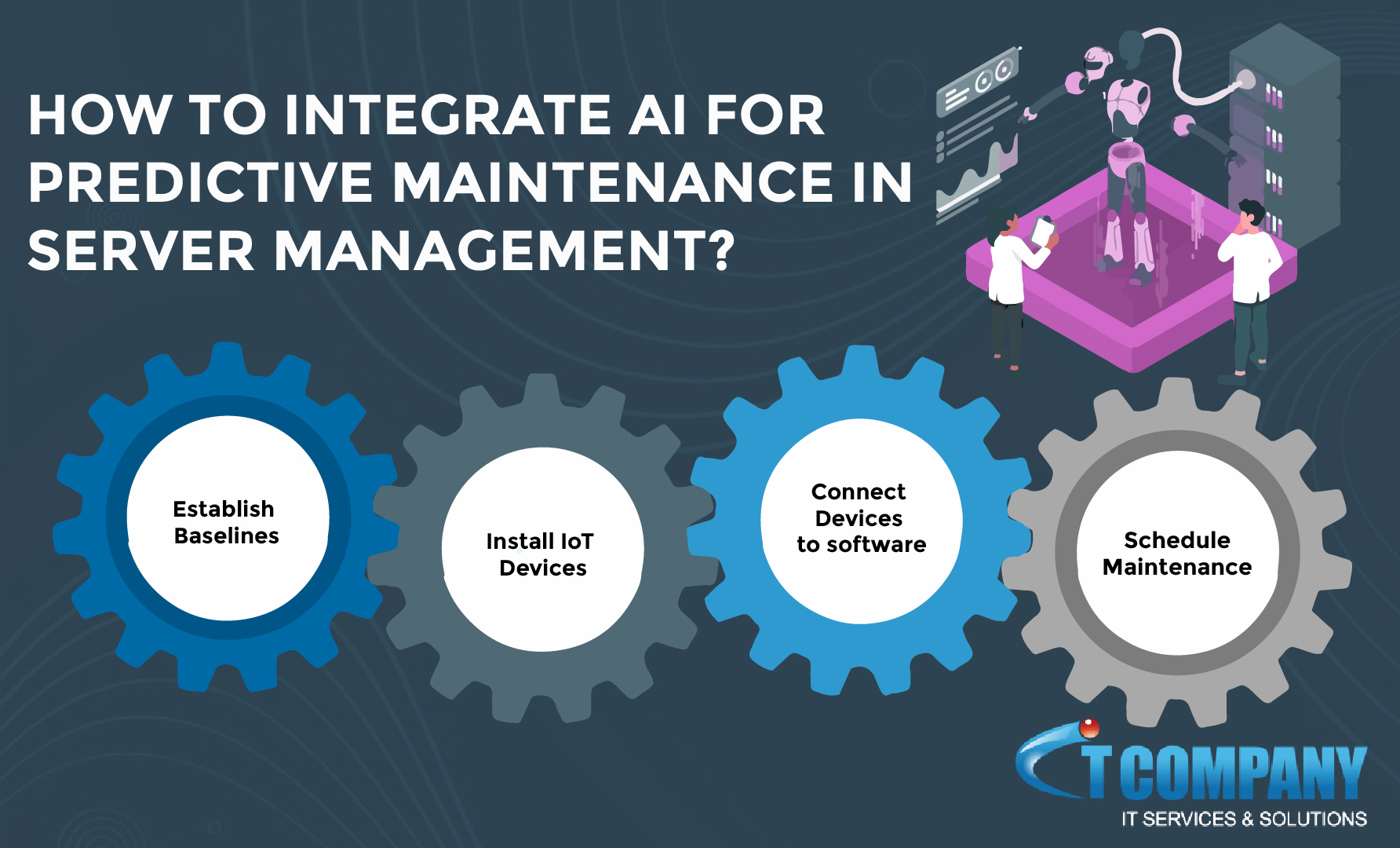
How to Integrate AI for Predictive Maintenance in Server Management
Server management is a critical aspect of any organization’s IT infrastructure. In today’s fast-paced digital world, the ability to predict server issues is crucial for maintaining uptime and reducing operational expenses. This is where the integration of artificial intelligence (AI) and predictive analytics can play a significant role. In this article, we will explore how…
-

How Cybercriminals Exploit GTM to Steal Data
The sun had barely risen when Jane, a small business owner running a boutique online store, opened her laptop to check sales. She had just launched a massive marketing campaign to boost her online presence. However, what she discovered instead was a nightmare. Her checkout pages, designed to capture customer payment details, had been hijacked.…
-

How to Fix Unwanted Indexed URLs
If you’re dealing with unwanted URL indexing in Google, you’re not alone. Many websites face this issue, especially when using dynamic URLs with query parameters, like ?add-to-cart. Google can crawl and index these URLs, even if you don’t want them to show up in search results. The usual advice includes using rel=canonical, robots.txt, or noindex…
-

Battle of AI Competition – The Most Powerful AI Tool
As it is said: “Artificial Intelligence is not a tool of the future—it’s the tool of today, transforming industries, enhancing human capabilities, and solving complex problems.” The most powerful AI tools are driving innovation, combining flexibility, advanced algorithms, and robust performance. From natural language processing to predicting the future, they never miss a beat. Winning…
-

Bidding Wars and Boring Ads -The Hidden Costs of Digital Marketing
In 2024, companies spent 13.2% more on digital advertising. But conversion rates dropped by 6.1%. What’s going wrong? The problem lies not just in rising costs but in how businesses approach digital marketing. Bidding wars, boring ads, and hidden costs are all silently eroding your profits. Let’s take a deeper dive into these challenges and…
-

Why DeepSeek is Better Than ChatGPT: The Ultimate Comparison
Artificial intelligence (AI) tools like DeepSeek and ChatGPT have transformed industries, but not all AI platforms are created equal. While ChatGPT has dominated the market, DeepSeek is emerging as a superior alternative. In this advanced comparison, we’ll dive deep into user statistics, technical architecture, open-source advantages, and real-world applications to prove why it outshines ChatGPT.…
-

5 Fastest Ways to Create 301 Redirects Quickly with Chat GPT
When you need to manage website redirects, especially 301 redirects, speed and efficiency are crucial. The process can be tedious, but with the right strategies, you can automate or simplify it significantly. Whether you are handling a few URLs or hundreds, here are five efficient ways to use ChatGPT to create 301 redirects quickly. What…
-

Google and AP Team Up to Enhance Gemini with Real-Time News Updates: What It Means for You
Google has formed a strategic partnership with The Associated Press (AP) to integrate real-time news into its generative AI platform, Gemini. This collaboration aims to offer accurate, up-to-the-minute news directly to users. Here’s a breakdown of what this means for the future of AI and news. Key Facts Key Points Details Partnership with AP Google…
-

Google’s Algorithms vs. AI-Generated Content: A Losing Battle?
The rise of AI tools like ChatGPT has revolutionized content creation. However, it has also raised questions about how search engines, particularly Google, handle AI-generated content. A recent case study by surferseo provides critical insights into Google’s algorithms and their ability to detect AI-written material. Case Study To explore whether Google’s search algorithms can distinguish…
-

Cloud Computing vs Cloud Storage: Understanding the Key Differences
Cloud computing and cloud storage are two pillars of modern technology, but knowing which one you truly need can make all the difference. While they may seem similar, they are actually quite different. In this article, we will explore the key differences between cloud computing and cloud storage, explain what each service offers, and help…